
Identity verification has become an integral part of our daily lives, with the rise of digital transactions and online services. However, traditional Know Your Customer (KYC) processes are often time-consuming, costly, and prone to errors. As technology continues to evolve, businesses are now exploring new and innovative alternatives to streamline identity verification processes and enhance security.
One of the most promising alternatives is the use of biometric data for identity verification. Biometrics, such as fingerprints, facial recognition, and iris scans, offer unique and highly secure methods of verifying a person’s identity. Unlike traditional methods, biometric data cannot be easily forged or stolen, making it an ideal solution for combating fraudulent activities and identity theft.
In addition to biometrics, blockchain technology is also being explored as a viable alternative for identity verification. The decentralized nature of blockchain ensures that sensitive user information is securely stored and cannot be tampered with. By leveraging blockchain, businesses can create a transparent and immutable identity verification system that eliminates the need for third-party intermediaries and reduces the risk of data breaches.
Another emerging alternative is the use of machine learning algorithms and artificial intelligence (AI) for identity verification. These technologies can analyze a vast amount of data and detect patterns and anomalies that may indicate fraudulent activities. By continuously learning and adapting, machine learning algorithms and AI systems can provide a more accurate and efficient means of identity verification, while also improving the overall user experience.
As the digital landscape continues to evolve, it is crucial for businesses to embrace new and innovative alternatives to traditional identity verification methods. Whether it’s biometrics, blockchain, or machine learning, these alternatives offer a more secure, cost-effective, and user-friendly approach to identity verification. By adopting these technologies, businesses can not only enhance security but also improve customer trust and confidence in their services.
The Importance of Identity Verification

Identity verification plays a crucial role in today’s digital age. With the increasing number of online transactions and interactions, ensuring the identity of individuals is of utmost importance. This is particularly relevant to industries such as banking, finance, and e-commerce, where the risk of fraud and identity theft is high.
Identity verification helps businesses establish trust and confidence with their customers. By verifying the identity of individuals, businesses can ensure that they are dealing with legitimate customers and reduce the risk of any fraudulent activities. It also helps in preventing the creation of fake accounts and unauthorized access to sensitive information.
Furthermore, identity verification is essential for compliance with legal and regulatory requirements. Know Your Customer (KYC) regulations, in particular, are designed to prevent money laundering, terrorism financing, and other illegal activities. By implementing effective identity verification processes, businesses can stay compliant with these regulations and avoid potential penalties and reputational damage.
As technology continues to advance, identity verification methods are also evolving. Traditional methods such as document checks and manual verification are being replaced by more advanced solutions like biometric identification, machine learning algorithms, and artificial intelligence. These alternative KYC methods offer increased accuracy, speed, and convenience, enabling businesses to verify identities more efficiently.
In conclusion, the importance of identity verification cannot be overstated. It not only helps businesses ensure the trustworthiness of their customers but also enables compliance with regulations and prevents fraudulent activities. As technology progresses, the future of identity verification looks promising, with innovative solutions aiming to streamline the process while maintaining the highest level of security.
Challenges with Traditional KYC Methods

Traditional Know Your Customer (KYC) methods have long been used by businesses to verify the identity of their customers. However, these methods come with a number of challenges and limitations that hinder their effectiveness.
1. Manual Verification Process
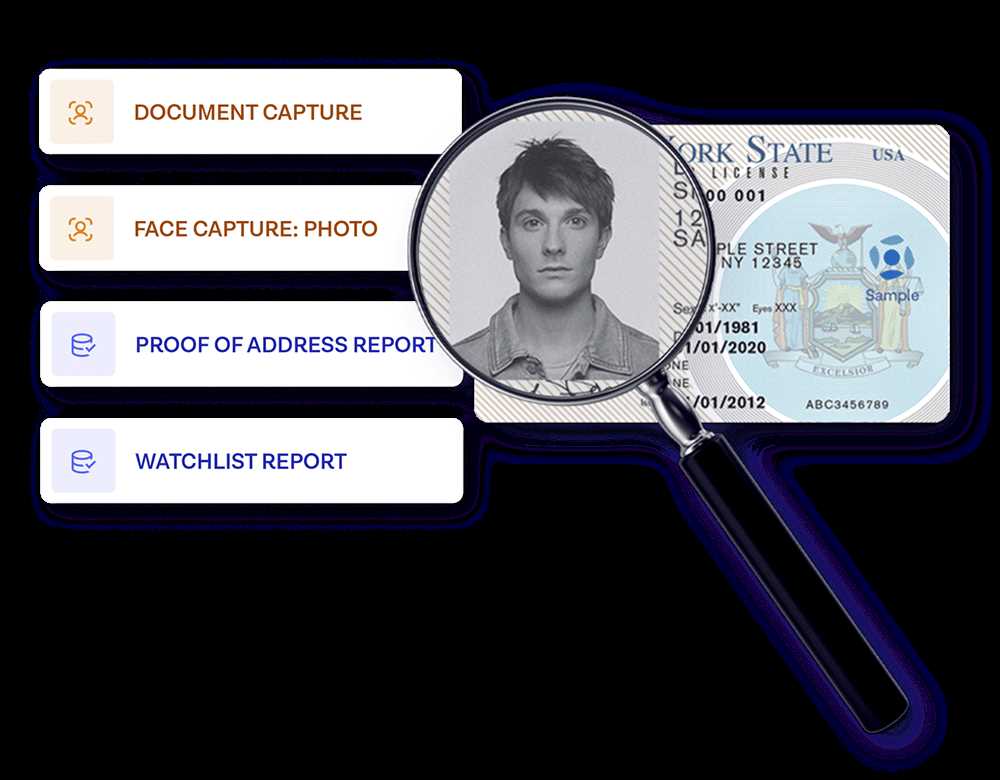
Traditional KYC methods involve a manual verification process, which requires customers to submit various identification documents such as passports, utility bills, and bank statements. This process is time-consuming and prone to human errors, as the verification is often done by employees who need to manually review and compare the documents provided. Moreover, the manual process can be costly for businesses as it requires dedicated resources for document storage and management.
2. Limited Accessibility
Another challenge with traditional KYC methods is limited accessibility for customers. Customers may need to physically visit a branch or provide physical copies of their documents, which can be inconvenient and time-consuming. This can lead to a drop in customer satisfaction and may deter potential customers from completing the verification process.
Furthermore, traditional KYC methods may not be accessible for individuals who do not have access to traditional banking services or physical identification documents. This poses a challenge for financial institutions and businesses that aim to provide services to underbanked populations or individuals living in remote areas.
3. Privacy Concerns

Traditional KYC methods rely on the collection and storage of sensitive personal data, raising privacy concerns. Customers may be hesitant to share their personal information, especially in light of recent high-profile data breaches and privacy scandals. Concerns about the misuse or mishandling of personal data can erode customer trust and loyalty.
Additionally, traditional KYC methods often require customers to provide multiple copies of their identification documents to different institutions or service providers. This increases the risk of identity theft and fraud, as these documents can potentially be intercepted or used without the customer’s knowledge.
Overall, while traditional KYC methods have been effective in the past, they are not without their challenges. As technology advances, businesses are exploring alternative solutions to address these challenges and improve the efficiency and security of identity verification processes.
Emerging Technologies in Identity Verification

As the need for secure and efficient identity verification continues to grow, emerging technologies are playing an increasingly important role in this field. These technologies are offering new and innovative ways to verify identity, while also addressing some of the key challenges associated with traditional methods of identity verification.
One emerging technology in this space is biometric authentication. Biometrics uses unique physical or behavioral characteristics, such as fingerprints, facial recognition, or iris scanning, to verify a person’s identity. This technology is highly accurate and difficult to forge, making it an attractive alternative to traditional identification documents.
Another technology that is gaining traction in identity verification is blockchain. Blockchain technology offers a decentralized and immutable way to store and verify identity information. By leveraging the power of cryptography and distributed ledger technology, blockchain can provide a secure and tamper-proof identity verification solution.
Artificial intelligence (AI) is also playing a significant role in identity verification. AI algorithms can analyze large amounts of data and detect patterns, anomalies, or potential fraud more effectively than manual methods. This technology can help streamline the identity verification process while also improving accuracy and reducing the risk of human error.
Mobile technology is another area where emerging technologies are making an impact. With the widespread adoption of smartphones, mobile devices are becoming a popular platform for identity verification. Mobile apps can utilize a combination of biometrics, AI, and secure communication protocols to provide convenient and secure identity verification services.
Furthermore, machine learning is being used to enhance identity verification systems by continuously learning and adapting to new threats and fraud patterns. Machine learning algorithms can analyze user data and behavior to detect suspicious activities and flag them for further investigation.
Overall, emerging technologies are revolutionizing the field of identity verification by offering new and more secure ways to establish and verify a person’s identity. These technologies have the potential to improve efficiency, enhance security, and provide a better user experience in the future of identity verification.
Biometric Authentication

Biometric authentication refers to the use of unique biological characteristics or behavioral patterns to verify a person’s identity. This method of identity verification has gained significant popularity in recent years due to its high level of accuracy and security.
One of the most commonly used biometric authentication methods is fingerprint recognition. Fingerprint patterns are unique to each individual and can be measured and analyzed using specialized biometric sensors. This technology has been widely adopted in mobile devices, enabling users to unlock their phones or authorize payments by simply scanning their fingerprints.
Another biometric authentication method is facial recognition. Facial recognition systems use advanced algorithms and cameras to analyze the unique features of a person’s face, such as the distance between their eyes, the shape of their nose, and the contours of their face. This technology is being used in various applications, such as access control systems and airport security checks.
Voice recognition is another type of biometric authentication that utilizes the unique characteristics of an individual’s voice, such as pitch, tone, and cadence. This technology is commonly used in phone-based authentication systems, where users are required to speak a specific phrase or answer a series of questions to verify their identity.
Biometric authentication offers several advantages over traditional identity verification methods. Firstly, it provides a higher level of security since biometric traits are difficult to forge or replicate. Additionally, it offers a more seamless user experience, as individuals can authenticate themselves using their own unique characteristics, eliminating the need to remember complicated passwords or PINs.
Despite its many benefits, biometric authentication does raise concerns regarding privacy and data security. The collection and storage of biometric data require robust security measures to prevent unauthorized access or misuse. Additionally, there is a need for clear regulations and guidelines to protect individuals’ biometric information and ensure its ethical and responsible use.
Conclusion

Biometric authentication provides a promising alternative to traditional identity verification methods. Its high accuracy and convenience make it a desirable solution for various industries, from finance and healthcare to travel and retail. However, it is important to carefully address and mitigate the privacy and security challenges associated with the implementation of biometric authentication systems.
Blockchain Technology

Blockchain technology is revolutionizing many industries, and identity verification is no exception. By leveraging the decentralized and immutable nature of blockchain, identity verification processes can become more secure, efficient, and privacy-centric.
One of the main advantages of using blockchain for identity verification is the elimination of centralized authorities. Traditional identity verification systems usually involve relying on a centralized entity, such as a government agency or a financial institution, to verify and store personal information. This centralization creates a single point of failure and increases the risk of data breaches and identity theft.
With blockchain technology, identity data can be securely stored and shared across a network of computers. Each participant in the network maintains a copy of the blockchain, ensuring that no single entity has control over the data. This distributed nature of blockchain makes it difficult for hackers to tamper with or gain unauthorized access to personal information.
Smart Contracts
In addition to decentralization, blockchain technology also enables the use of smart contracts for identity verification. Smart contracts are self-executing contracts with the terms of the agreement directly written into code. These contracts are stored on the blockchain and automatically enforce the agreed-upon conditions.
For identity verification purposes, smart contracts can be designed to facilitate the exchange of verified personal information between individuals and service providers. Users can grant selective access to their verified identity data, allowing service providers to confirm their identity without needing to collect and store their personal information.
Interoperability and Portability

Another benefit of using blockchain technology for identity verification is the potential for interoperability and portability. Different identity verification systems can adopt blockchain standards, allowing for seamless sharing and verification of identity data across various platforms and services. This interoperability can simplify the onboarding process for users, as they can reuse their verified identity across multiple applications.
| Benefits of Blockchain for Identity Verification | Challenges |
|---|---|
| – Decentralization | – Scalability |
| – Security | – Regulatory Compliance |
| – Privacy | – Adoption |
| – Efficiency | – User Experience |
In conclusion, blockchain technology holds great promise for the future of identity verification. Its decentralized nature, combined with smart contracts and interoperability, can address many of the current challenges in traditional identity verification systems. As blockchain continues to evolve and mature, we can expect to see more widespread adoption of blockchain-based identity verification solutions.
Advantages and Disadvantages of KYC Alternatives
Advantages:
1. Enhanced privacy: KYC alternatives can offer enhanced privacy for individuals as their personal information isn’t stored or shared with multiple organizations. This can help protect individuals’ identity and reduce the risk of data breaches.
2. Cost-effective: KYC alternatives can be more cost-effective for businesses compared to traditional KYC processes. They eliminate the need for manual verification and can streamline the onboarding process, reducing operational costs.
3. Faster onboarding: KYC alternatives often involve automated processes that can significantly speed up the onboarding process for customers. This can help businesses improve customer experience and reduce abandonment rates.
Disadvantages:
1. Limited acceptance: KYC alternatives may not be widely accepted by all organizations, especially in highly regulated industries. This can create challenges for individuals who need to provide KYC information to multiple parties.
2. Reliability concerns: There may be concerns about the reliability and accuracy of KYC alternatives compared to traditional KYC processes. Businesses need to ensure that the alternative methods they choose are robust and provide accurate results.
3. Lack of standardization: The lack of standardization across different KYC alternatives can create interoperability issues. Different organizations may have different requirements and approaches, making it difficult for individuals to navigate the process smoothly.
Question-answer:
What is KYC and why is it important?
KYC stands for Know Your Customer, and it is a process used by businesses to verify the identity of their customers. It is important because it helps businesses comply with regulations, prevent fraud, and ensure the security of their services.
What are some of the challenges with traditional KYC methods?
Traditional KYC methods often require customers to provide physical identification documents, which can be time-consuming, costly, and prone to errors. Additionally, storing and managing large amounts of customer data can create data privacy and security concerns.
What are some alternative methods to traditional KYC?
Some alternative methods to traditional KYC include remote identity verification through video calls, the use of biometric data such as fingerprints or facial recognition, and the use of blockchain technology to securely store and share customer identity information.
How can remote identity verification through video calls be a reliable alternative to traditional KYC?
Remote identity verification through video calls allows businesses to verify a customer’s identity in real-time, providing a more seamless and convenient experience for both the customer and the business. By utilizing advanced facial recognition technology and document scanning, remote identity verification can be just as reliable as traditional methods.
What are the potential benefits of using blockchain technology for identity verification?
Using blockchain technology for identity verification can provide increased security, transparency, and control over personal data. It can also streamline the verification process by enabling individuals to securely share their verified identity information with multiple organizations, eliminating the need for multiple verification processes.


