
When it comes to online data security, user confidentiality is of utmost importance. With the rising number of data breaches and privacy concerns, individuals and organizations have become increasingly cautious about sharing their sensitive information. However, traditional encryption methods are no longer sufficient to guarantee the full protection of user data.
Introducing Galxe Protocol’s revolutionary solution – Zero-Knowledge Proofs. With Zero-Knowledge Proofs, users can securely authenticate their identity and validate their data without revealing any confidential information. This breakthrough technology allows individuals to maintain complete control over their personal data, giving them peace of mind in an age of digital vulnerability.
Unlike traditional encryption methods, Zero-Knowledge Proofs operate on the principle of verifying information without requiring the sender to disclose any specific details. This means that users can perform transactions, access services, or prove their identity without revealing their private information to third parties or even to the service provider themselves.
The Galxe Protocol’s Zero-Knowledge Proofs provide a unique solution to the ongoing challenge of protecting user confidentiality. By ensuring that private information remains private, individuals and organizations can confidently engage in online activities without compromising their sensitive data. With this cutting-edge technology, Galxe Protocol is paving the way for a safer and more secure digital future.
The Importance of User Confidentiality

User confidentiality is a fundamental aspect of maintaining trust and ensuring privacy in the digital age. With the increasing frequency and sophistication of cyberattacks, protecting user data has become paramount. Galxe Protocol’s Zero-Knowledge Proofs provide a significant advancement in safeguarding user confidentiality.
Preserving Personal Information
Preserving user confidentiality means safeguarding personal information from unauthorized access or disclosure. By leveraging Galxe Protocol’s Zero-Knowledge Proofs, sensitive user data such as passwords, credit card details, and personal identifiers can remain encrypted and hidden from prying eyes.
This level of protection ensures that the confidentiality of personal information remains intact, maintaining the trust between users and service providers. It allows users to freely interact with digital platforms without the fear that their data may be compromised.
Enhancing User Privacy
User confidentiality also encompasses the notion of privacy. Individuals have the right to keep their online activities private and control the dissemination of their personal information. Galxe Protocol’s Zero-Knowledge Proofs enable users to maintain their privacy by providing a secure and anonymous means of interacting with online platforms.
Through Zero-Knowledge Proofs, users can prove ownership or the validity of certain information without revealing any sensitive data. This enhances privacy by minimizing the amount of personal information that needs to be shared, reducing the risk of data breaches and identity theft.
Overall, user confidentiality is crucial in maintaining trust and ensuring privacy in the digital world. Galxe Protocol’s Zero-Knowledge Proofs play a pivotal role in preserving personal information and enhancing user privacy, laying the foundation for a more secure and trustworthy digital ecosystem.
Ensuring Privacy in the Digital Age
In today’s digital age, where personal data is constantly being shared, collected, and analyzed, ensuring privacy has become a significant concern. With the advancement of technology, various platforms, and devices, the need to protect user confidentiality has become more critical than ever.
Many individuals are unaware of the vast amount of personal information they inadvertently share online. From social media posts and online shopping habits to browsing history and location data, a vast digital footprint is left behind on a daily basis.
This accumulation of personal data has opened doors for various entities, including governments, companies, and hackers, to access and exploit individuals’ private information. Breaches, data leaks, and cyber-attacks have become commonplace, resulting in rampant identity theft and misuse of personal data.
The Importance of Privacy

Privacy is a fundamental human right and plays a significant role in maintaining personal autonomy and freedom. Concrete steps need to be taken to protect individuals’ privacy and confidentiality, mitigating the risks associated with the digital age.
Respecting privacy ensures that individuals have control over their personal information, decide how it is utilized, and maintain the right to be forgotten. It provides a sense of security and allows individuals to express themselves freely without fear of surveillance or judgment.
The Role of Zero-Knowledge Proofs
Zero-knowledge proofs, such as the Galxe Protocol’s innovative solution, offer a promising approach to protect user confidentiality in the digital age. These proofs allow individuals to prove the truth of a statement without revealing any additional information along with it.
By implementing zero-knowledge proofs, individuals can securely authenticate their identity, perform transactions, and exchange sensitive information without disclosing any details that may compromise their privacy. This privacy-centric approach enhances trust and ensures that only authorized entities have access to sensitive data.
With the continuous advancements in technology and the growing importance of privacy, the implementation of robust privacy measures, such as zero-knowledge proofs, is crucial. It is essential to prioritize the development and adoption of these solutions to ensure privacy in the digital age and empower individuals to take control of their personal data.
In conclusion, ensuring privacy in the digital age is of utmost importance. With the increasing challenges related to the collection and exploitation of personal data, the adoption of privacy-centric approaches, such as zero-knowledge proofs, is necessary to protect user confidentiality and maintain the fundamental right to privacy.
The Risks of Data Breaches

Data breaches pose major risks to both individuals and organizations. These breaches occur when unauthorized parties gain access to sensitive information, such as personal data or financial records. The consequences of data breaches can be severe and far-reaching, impacting both the victims and the entities responsible for safeguarding the data.
1. Financial Loss
Data breaches can result in significant financial losses for individuals and businesses. Stolen financial information, such as credit card details or bank account numbers, can be used for fraudulent activities, leading to unauthorized transactions and drained accounts. Organizations may also face financial liabilities, including legal fees and regulatory fines, as a result of failing to protect user data.
2. Identity Theft
One of the most serious risks associated with data breaches is identity theft. Cybercriminals can use stolen personal information, such as social security numbers or addresses, to create fake identities or carry out fraudulent activities. This can lead to financial ruin, damaged credit scores, and the need for extensive identity theft recovery efforts.
3. Damage to Reputations

Data breaches can cause significant damage to an individual’s or organization’s reputation. When personal or confidential information is compromised, trust is broken, and customers may lose confidence in the affected entity’s ability to protect their data. This can result in a loss of business, diminished brand value, and long-term reputational damage.
4. Legal and Regulatory Consequences
Data breaches can have legal and regulatory consequences for organizations. Depending on the jurisdiction and the nature of the breach, companies may be required to notify affected individuals, regulators, and law enforcement agencies. Failure to comply with data protection laws and regulations can lead to hefty fines and legal penalties.
In conclusion, data breaches present serious risks to individuals and organizations. The financial loss, identity theft, damage to reputations, and legal consequences that can result from a breach highlight the importance of robust data protection measures and proactive efforts to safeguard sensitive information.
Consequences of Personal Information Exposure

In today’s digital age, personal information is increasingly at risk of being exposed to unauthorized parties. When personal information falls into the wrong hands, it can have severe consequences for individuals. This section explores some of the potential consequences of personal information exposure.
Identity Theft: One of the most significant consequences of personal information exposure is the risk of identity theft. If an individual’s personal information, such as their social security number, credit card details, or even biometric data, is exposed, malicious actors can use this information to impersonate the individual, open fraudulent accounts, or make unauthorized purchases in their name.
Financial Loss: Personal information exposure can lead to financial loss for affected individuals. Cybercriminals can use stolen information to gain access to bank accounts, credit card accounts, or other financial assets, resulting in unauthorized transactions and drained funds. Victims of personal information exposure may also face difficulties in recovering their lost finances and restoring their identity.
Reputation Damage: Personal information exposure can also result in severe damage to an individual’s reputation. If sensitive information, such as personal photos, emails, or messages, is leaked, it can be exploited or used against the individual. This can lead to social embarrassment, public humiliation, or even the loss of personal and professional relationships.
Privacy Invasion: Personal information exposure often results in a significant invasion of privacy. Once personal information is compromised, it becomes difficult to regain control over one’s privacy. Individuals may experience constant monitoring, targeted advertising, or even harassment due to the exposed information.
Legal and Regulatory Consequences: Depending on the nature of the personal information exposed, individuals and organizations may face legal and regulatory consequences. Data protection laws, such as the GDPR in European countries or the CCPA in the United States, impose penalties for data breaches and unauthorized disclosure of personal information. This can result in reputation damage, financial penalties, or even legal action against the responsible parties.
Psychological Impact: Finally, personal information exposure can have a significant psychological impact on individuals. The fear, anxiety, and stress resulting from the violation of privacy can lead to psychological distress and long-lasting consequences for the affected individuals. It is essential to prioritize user confidentiality and adopt technologies that protect personal information to avoid these negative psychological effects.
In conclusion, the consequences of personal information exposure are far-reaching and can have severe implications for individuals. Protecting user privacy and implementing robust security measures, such as zero-knowledge proofs, is crucial in today’s digital landscape to mitigate the risks of personal information exposure and safeguard user confidentially effectively.
Introducing Galxe Protocol’s Zero-Knowledge Proofs

As technology continues to advance, the issue of user confidentiality and data privacy becomes increasingly important. Users want to know that their personal information is secure and inaccessible to unauthorized parties. To address this concern, Galxe Protocol is proud to introduce its innovative solution: Zero-Knowledge Proofs.
Zero-Knowledge Proofs are a cryptographic method that allows a user to prove the authenticity of certain information without revealing the actual data itself. With this approach, Galxe Protocol ensures that user confidentiality remains intact, while still providing the necessary verification.
How does Zero-Knowledge Proofs work? Using advanced mathematics and algorithms, Galxe Protocol is able to create proofs that demonstrate the validity of a statement without revealing the actual underlying data. This means that a user can verify their identity or other sensitive information without exposing any details to an outside party.
The benefits of Zero-Knowledge Proofs are numerous. First and foremost, it ensures that user data and confidential information are protected from unauthorized access. By allowing users to prove their identity or other credentials without revealing the actual data, Galxe Protocol provides an added layer of security.
Additionally, Zero-Knowledge Proofs also contribute to increased trust and transparency. Users can feel confident that their information is being handled securely and that they have control over what data is shared. This fosters a sense of trust between Galxe Protocol and its users, leading to a stronger and more reliable relationship.
Galxe Protocol’s Zero-Knowledge Proofs represent a significant step in protecting user confidentiality and data privacy. By combining advanced mathematics with cutting-edge technology, Galxe Protocol is able to provide an innovative solution that ensures user data remains secure. With the introduction of Zero-Knowledge Proofs, Galxe Protocol reaffirms its commitment to putting user confidentiality first.
With this groundbreaking technology, Galxe Protocol is leading the way in protecting user confidentiality and privacy. By introducing Zero-Knowledge Proofs, Galxe Protocol is revolutionizing the way data is verified and authenticated, setting a new standard for user security in the digital age.
What are Zero-Knowledge Proofs
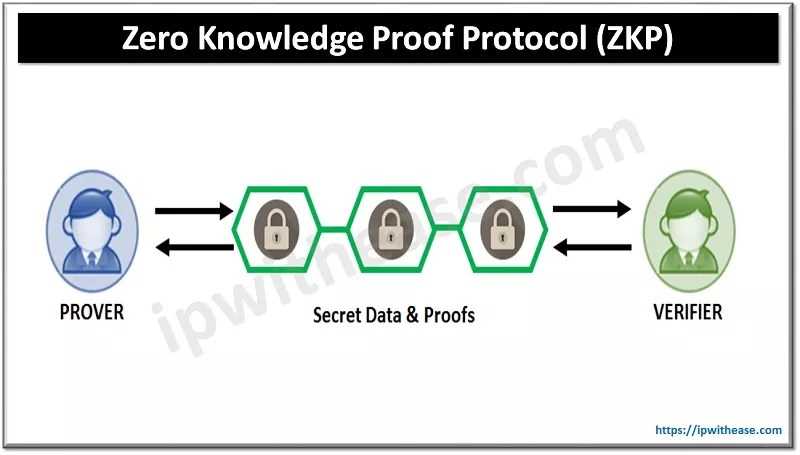
Zero-Knowledge Proofs are a cryptographic concept that allows one party, the prover, to prove to another party, the verifier, that a certain statement is true, without revealing any additional information apart from the fact that the statement is indeed true. In other words, a zero-knowledge proof enables a prover to convince a verifier of the validity of a statement while preserving the confidentiality of the underlying data.
This powerful cryptographic technique ensures that sensitive information remains private and confidential. Zero-knowledge proofs achieve this by employing advanced mathematical algorithms that allow the prover to demonstrate knowledge of a secret or a fact, without disclosing the specifics of the secret or fact itself.
Zero-knowledge proofs have a wide range of applications in various fields, including blockchain technology, secure communication protocols, and authentication systems. By leveraging zero-knowledge proofs, organizations can protect user confidentiality, verify data integrity, and establish trust in their systems without compromising privacy.
Overall, zero-knowledge proofs play a crucial role in ensuring the privacy and security of sensitive information, enabling secure interactions in digital environments while preserving confidentiality.
How Galxe Protocol Implements Zero-Knowledge Proofs
The Galxe Protocol is at the forefront of protecting user confidentiality through its implementation of Zero-Knowledge Proofs. By utilizing this advanced cryptographic technique, Galxe Protocol ensures that sensitive user information remains private and secure.
Zero-Knowledge Proofs work by allowing parties to prove the validity of a statement without revealing any additional information beyond what is necessary. In the case of Galxe Protocol, this means that users can prove their identity or possession of certain credentials without disclosing any personal data.
Generating and Verifying Zero-Knowledge Proofs
When a user wants to authenticate themselves or provide proof of ownership, Galxe Protocol generates a Zero-Knowledge Proof based on the user’s input and the system’s secret parameters. This proof is then provided to the verifying party, who can verify its authenticity without gaining any further knowledge.
During the verification process, the verifying party uses the Zero-Knowledge Proof and the existing system parameters to check its validity. If the proof passes the verification process, the verifying party is assured that the user’s claim is valid without learning any additional information.
Protecting User Confidentiality
The implementation of Zero-Knowledge Proofs in Galxe Protocol ensures that user confidentiality is protected at all times. Since the proof does not reveal any sensitive information, users’ personal data cannot be compromised or used maliciously.
| Benefits of Galxe Protocol’s Zero-Knowledge Proofs |
|---|
| 1. Enhanced Privacy: User confidentiality is maintained by only verifying necessary information. |
| 2. Security: Zero-Knowledge Proofs provide a high level of security, protecting against unauthorized access or data breaches. |
| 3. Trustworthy Authentication: The use of Zero-Knowledge Proofs ensures that users can authenticate themselves without compromising their personal data. |
In conclusion, Galxe Protocol’s implementation of Zero-Knowledge Proofs is a crucial element in protecting user confidentiality. By using this advanced cryptographic technique, Galxe Protocol ensures that sensitive information remains private and secure, providing users with enhanced privacy and trustworthy authentication.
Question-answer:
What is Galxe Protocol’s Zero-Knowledge Proofs?
Galxe Protocol’s Zero-Knowledge Proofs is a data privacy solution that allows users to share information without revealing the actual data. It uses cryptographic techniques to prove the validity of a statement without disclosing any sensitive information.
How does Galxe Protocol’s Zero-Knowledge Proofs protect user confidentiality?
Galxe Protocol’s Zero-Knowledge Proofs ensure user confidentiality by allowing users to prove the validity of a statement without revealing any actual data. This is achieved through cryptographic techniques that enable one party to verify the veracity of a claim made by another party, without learning any additional information about the claim.
Can you give an example of how Galxe Protocol’s Zero-Knowledge Proofs can be used?
Sure! Let’s say you want to prove that you are over 18 years old to access a certain website, but you don’t want to disclose your actual age. With Galxe Protocol’s Zero-Knowledge Proofs, you can prove that you are over 18 without revealing your exact age. This protects your confidentiality while still allowing you to access the desired service.


