In today’s digital world, the threat of Sybil attacks looms large. These malicious attacks, where a single entity creates multiple fake identities to gain control over a network, can cause widespread damage and undermine the trust users have in online platforms. With the rise of decentralized technologies like blockchain, it has become even more critical to protect against Sybil attacks.
Galxe’s Web3 Credentials offer a powerful solution to this problem. By leveraging the unique properties of blockchain technology, Galxe ensures that each user has a verified and tamper-proof identity. This identity is linked to a user’s Web3 wallet, creating a seamless and secure way to authenticate users and prevent Sybil attacks.
With Galxe’s Web3 Credentials, users have the ability to prove their identity without revealing any personal or sensitive information. This not only protects users from potential data breaches but also ensures that the verification process is efficient and transparent. By utilizing advanced cryptographic techniques and decentralized consensus, Galxe makes it virtually impossible for an attacker to create multiple fake identities.
Furthermore, Galxe’s Web3 Credentials can be easily integrated into existing platforms and applications. Whether it’s a decentralized exchange, a social media platform, or an e-commerce website, Galxe’s solution provides a robust and scalable way to prevent Sybil attacks. By implementing this technology, platforms can restore trust and ensure that their users can interact in a secure and trustworthy environment.
In conclusion, protecting against Sybil attacks is of utmost importance in today’s digital landscape. Galxe’s Web3 Credentials offer a reliable and efficient solution to this problem, leveraging the power of blockchain to verify user identities and prevent malicious attacks. By adopting this technology, platforms can create a more secure and trustworthy online experience for their users, ultimately fostering the growth of a decentralized and inclusive digital ecosystem.
The Growing Threat of Sybil Attacks
Sybil attacks pose a significant threat to the security and integrity of online networks and systems. Named after the famous psychiatric patient, Shirley Ardell Mason, who had multiple personalities, Sybil attacks involve the creation of multiple fake or impersonated identities to gain control or influence over a network.
How Sybil Attacks Work

In a Sybil attack, an attacker creates multiple accounts that appear to be distinct individuals, but are actually controlled by a single entity. These fake accounts can then be used to manipulate online systems, spread fake information, or launch coordinated attacks.
One common example of a Sybil attack is in social media platforms, where an attacker creates multiple accounts to generate a false consensus or amplify a particular message. By appearing to be multiple individuals supporting a cause or viewpoint, the attacker can influence public opinion or spread misinformation.
The Dangers of Sybil Attacks
Sybil attacks can have serious consequences in various contexts:
- Blockchain: In blockchain networks, Sybil attacks can allow an attacker to control a significant portion of the network’s computing power, leading to 51% attacks, double-spending, or other forms of manipulation.
- Online Communities: In online communities and forums, Sybil attacks can disrupt conversations, spread false information, and manipulate discussions, undermining trust and collaboration.
- Online Voting Systems: Sybil attacks can undermine the integrity of online voting systems, allowing an attacker to create multiple fake identities and influence the outcome of elections.
The growing adoption of decentralized technologies and the rise of social media platforms make the threat of Sybil attacks more relevant than ever before. It is imperative for developers and users to implement strong security measures to protect against these attacks and preserve the integrity of online ecosystems.
Understanding the Concept of Sybil Attacks

Sybil attacks are a type of security threat that occurs in decentralized networks, such as blockchain and peer-to-peer systems. In a Sybil attack, an attacker creates multiple identities or nodes to gain control or subvert the network’s operations.
How Sybil Attacks Work
In a Sybil attack, the attacker compromises the network’s trust by creating multiple fake identities, also known as Sybil nodes. These nodes can be controlled by a single entity but appear as separate entities in the network. The attacker uses these Sybil nodes to perform malicious activities, manipulate network operations, and gain disproportionate influence over the network.
Purposes and Consequences of Sybil Attacks
Sybil attacks can have various purposes and consequences, depending on the attacker’s objectives. Some common goals of Sybil attacks include:
- Controlling voting systems to manipulate outcomes.
- Creating a false sense of consensus or popularity.
- Disrupting network operations or services.
- Gaining unfair advantages, such as mining rewards or privileges.
These attacks can harm the integrity and security of decentralized networks, undermining their core principles, such as trust, transparency, and decentralization. Sybil attacks can also lead to decreased user trust, decreased network performance, and increased vulnerability to other types of attacks.
The Impact of Sybil Attacks on Web3 Security

Sybil attacks pose a significant threat to the security of Web3, and it is crucial for users and developers to understand the potential impact.
What is a Sybil Attack?

A Sybil attack occurs when an individual or entity creates multiple fake identities to deceive a network or system. These fake identities, known as Sybil nodes, allow attackers to gain control over a majority of a network’s resources or influence its decision-making process.
Web3 relies on decentralized networks and peer-to-peer interactions, making it susceptible to Sybil attacks. In the absence of a central authority or trusted third-party, nodes within the network must rely on consensus algorithms to validate transactions and maintain security.
The Risks and Consequences

The impact of a successful Sybil attack can be severe and wide-ranging. Here are some potential risks and consequences:
1. Manipulation of Consensus: Sybil attacks can manipulate the consensus mechanism of a Web3 network, potentially leading to fraudulent transactions, tampering with data integrity, or even the creation of a parallel chain.
2. Denial of Service (DoS) Attacks: Sybil nodes can overwhelm a network with a large number of fake identities, consuming excessive resources and causing a denial of service to legitimate users. This can disrupt the functionality and availability of Web3 services.
3. Breach of Privacy: Sybil attacks can compromise the privacy of Web3 users by enabling attackers to gain access to sensitive information, such as transaction details or personal data.
Protecting Against Sybil Attacks
Given the potential impact of Sybil attacks, it is essential to implement robust security measures to mitigate these risks. Some strategies include:
1. Identity Verification: Implementing identity verification mechanisms can help ensure that only legitimate users are allowed to participate in a Web3 network.
2. Reputation Systems: Reputation systems can be used to build trust within the network by evaluating the behavior and interactions of participants. This can help identify and mitigate the presence of Sybil nodes.
3. Network Analysis: Analyzing network traffic and behavior patterns can detect anomalies and suspicious activities that may indicate the presence of Sybil attacks. This can aid in the prompt detection and response to potential threats.
By understanding the risks and implementing appropriate security measures, the Web3 ecosystem can better protect itself against Sybil attacks and ensure the integrity, privacy, and availability of its services.
Introducing Galxe’s Web3 Credentials
With Galxe’s Web3 Credentials, users can now authenticate themselves securely using the power of blockchain technology. This decentralized approach eliminates the need for a central authority to verify user identities, making it virtually impossible for Sybil attacks to occur.
Web3 Credentials are built on the principles of transparency, immutability, and trust. Each user’s credentials are stored securely on the blockchain, ensuring that they cannot be tampered with or manipulated. This gives developers and service providers the confidence that they are interacting with genuine users, enhancing the overall security of Web3 applications.
Galxe’s innovative solution also offers seamless integration with existing Web3 protocols, making it easy for developers to incorporate Web3 Credentials into their applications. This means that developers can focus on building robust and secure applications without worrying about the complexities of identity verification.
What sets Galxe’s Web3 Credentials apart is their ability to create a unique digital identity for each user. These credentials can include various attributes, such as verified email addresses, social media profiles, or even proof of ownership of specific assets. This multi-factor authentication strengthens the trustworthiness of user identities, further mitigating the risk of Sybil attacks.
By leveraging the power of blockchain and cryptographic techniques, Galxe’s Web3 Credentials offer a scalable and efficient solution to protect against Sybil attacks. With the rise of Web3 applications, it is crucial to have robust identity verification mechanisms in place, and Galxe’s Web3 Credentials provide just that.
With the introduction of Galxe’s Web3 Credentials, the Web3 ecosystem takes a significant step forward in ensuring the security and trustworthiness of its users. As the threat of Sybil attacks continues to evolve, Galxe remains at the forefront, providing cutting-edge solutions to protect against them.
Trust Galxe’s Web3 Credentials for a secure and reliable Web3 experience!
How Galxe’s Web3 Credentials Protect Against Sybil Attacks
Web3 credentials play a crucial role in protecting against Sybil attacks in the Galxe ecosystem. Sybil attacks occur when a malicious actor creates multiple fake identities to gain control or influence over a network. These attacks can compromise the integrity and trustworthiness of a decentralized system.
Galxe’s Web3 credentials act as a robust mechanism to prevent Sybil attacks by requiring users to verify their identity. By using cryptographic techniques such as public-private key pairs, users can generate a unique digital signature that proves their authenticity.
Immutable Identity
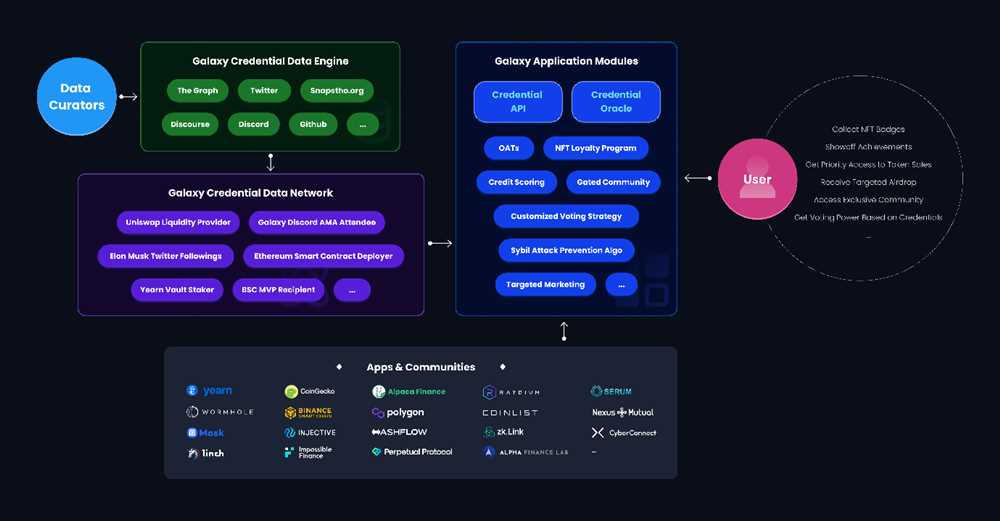
Galxe’s Web3 credentials link users’ digital identities to their real-world identity, making it challenging for attackers to create multiple fake accounts. Each user is assigned a unique Ethereum address that serves as their immutable identity on the Galxe platform.
Furthermore, the decentralized nature of Galxe ensures that these identities are recorded on the Ethereum blockchain, making it virtually impossible for malicious actors to tamper with or forge them.
Trust and Reputation

Galxe’s Web3 credentials also enhance trust and reputation within the ecosystem. Users’ verified identities create a sense of accountability, as their actions can be traced back to their Ethereum addresses.
Additionally, the Galxe platform incorporates reputation systems that leverage Web3 credentials. Users with a strong track record of honest and reliable behavior are more likely to gain trust and receive opportunities within the ecosystem.
Overall, Galxe’s Web3 credentials provide a secure and reliable foundation to protect against Sybil attacks. By linking users’ digital identities to real-world identities and promoting accountability, Galxe establishes a trustworthy environment for users to participate and contribute to the ecosystem.
The Benefits of Using Galxe’s Web3 Credentials

Increased Security: Galxe’s Web3 Credentials provide a secure way to verify and authenticate user identity in a decentralized network. By utilizing cryptographic signatures and public-key infrastructure, Galxe’s solution significantly reduces the risk of Sybil attacks and other forms of identity fraud.
Improved Trust: With Galxe’s Web3 Credentials, users can trust that they are interacting with verified and trustworthy individuals or organizations. By leveraging blockchain technology and decentralized identity, Galxe builds a reputation system that helps users make informed decisions about whom to engage with.
Enhanced Privacy: Galxe’s Web3 Credentials prioritize user privacy by allowing individuals to control their own data. Users have the power to selectively disclose specific information without revealing their entire identity, giving them more control over their personal information and reducing the risk of data breaches.
Streamlined User Experience: Galxe’s Web3 Credentials simplify the user experience by providing a single, universal identity for accessing various decentralized applications. Users no longer need to manage multiple accounts and passwords across different platforms, reducing complexity and improving convenience.
Interoperability: Galxe’s Web3 Credentials are designed to be compatible with existing web standards, making it easier for developers to integrate them into their applications. This interoperability enhances the usability and adoption of Galxe’s solution across different platforms and networks.
Future-Proof Technology: Galxe’s Web3 Credentials are built on cutting-edge blockchain and decentralized identity technologies, ensuring long-term viability and adaptability. By staying at the forefront of innovation, Galxe’s solution can continue to provide secure and reliable Web3 Credentials as the technology landscape evolves.
Question-answer:
What is a Sybil attack?
A Sybil attack is a type of attack where an attacker creates multiple identities or accounts to gain control over a network or system. This allows the attacker to manipulate the network or system in their favor.
How does Galxe’s Web3 Credentials protect against Sybil attacks?
Galxe’s Web3 Credentials provide a decentralized identity framework that ensures the identity of participants in a network. This prevents Sybil attacks by verifying the authenticity of each identity and allowing trusted interactions within the network.
What are the benefits of using Galxe’s Web3 Credentials?
Using Galxe’s Web3 Credentials provides several benefits. It ensures secure and trusted interactions within a network, protects against Sybil attacks, and allows for decentralized identity management. Additionally, it provides privacy and ownership control over personal data.
Can Galxe’s Web3 Credentials be used in any type of network or system?
Yes, Galxe’s Web3 Credentials can be used in any type of network or system. Its decentralized identity framework is applicable to various industries and use cases, including finance, healthcare, supply chain, and more.
Is Galxe’s Web3 Credentials compatible with existing identity management systems?
Yes, Galxe’s Web3 Credentials is designed to be interoperable with existing identity management systems. It can integrate with traditional systems to provide enhanced security and privacy while maintaining compatibility.


